Predictive Domain Intelligence
Stop phishing attacks before they exist
Identify malicious infrastructure intent at the moment of domain creation — before emails are sent or sites go live.
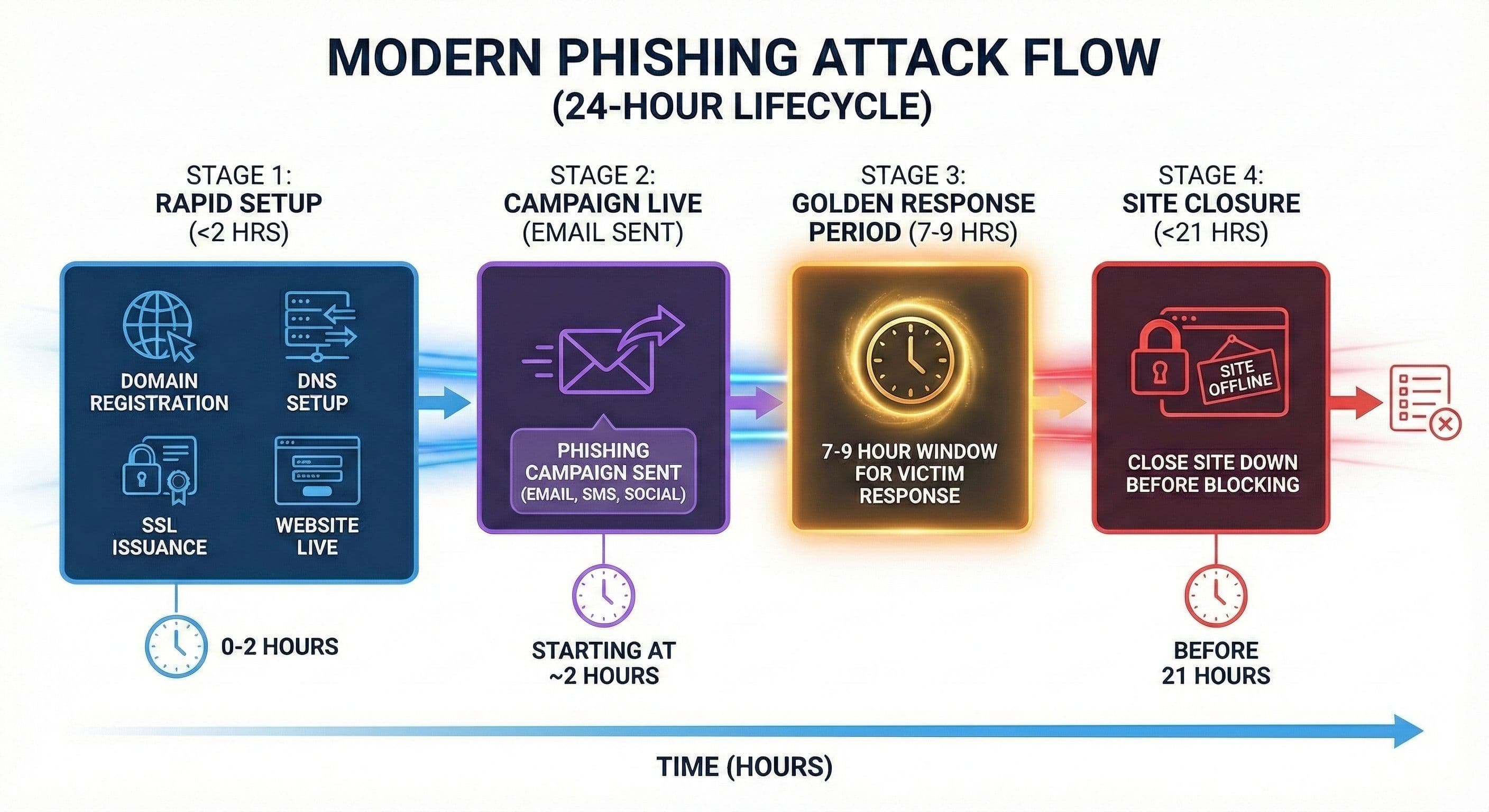
Modern Threats Move Fast - Infrastructure Moves First
Attackers don’t start with emails or websites. They start by assembling infrastructure.
Domains are registered, routing paths are manipulated, DNS is configured, and certificates are issued — often within minutes. Traditional security tools don’t see this stage because they’re watching the wrong layer.
By the time content appears or users report abuse, the campaign is already underway.
The Only Real Prevention Window
The only reliable opportunity to stop phishing is during infrastructure setup — before emails are sent and before sites are indexed.
Datazag identifies malicious intent as infrastructure is created, not after it’s abused.
By correlating routing anomalies, DNS behavior, and certificate issuance in real time, Datazag generates enforcement-ready alerts in under 60 seconds, while the attack is still forming.
Our Approach:
Why Infrastructure-level Intelligence is Critical
Phishing exposes a fundamental mismatch in modern security:
- Attacks originate at the infrastructure layer
- Detection still happens at the content layer
What traditional tools do:
- Wait for emails to be sent
- Wait for sites to be reported
- React after damage occurs
This isn’t just a phishing problem — it applies to:
- Phishing infrastructure (live for hours, then abandoned)
- Command & control environments
- Payment fraud and scam networks
- Email abuse and spoofing infrastructure
Once content exists, the prevention window is already closing.
What this means:
- Attackers register domains, configure DNS, obtain SSL certificates
- Traditional security tools wait for emails to be sent or websites to be reported
- By the time detection happens, attacks have succeeded
This pattern repeats across all infrastructure-based threats:
- Phishing domains (live 21 hours, then abandoned)
- C2 infrastructure (ephemeral command & control)
- Fraud campaigns (disposable sites for payment scams)
- Email abuse (spoofed sender infrastructure)
The key prevention window is during infrastructure setup.
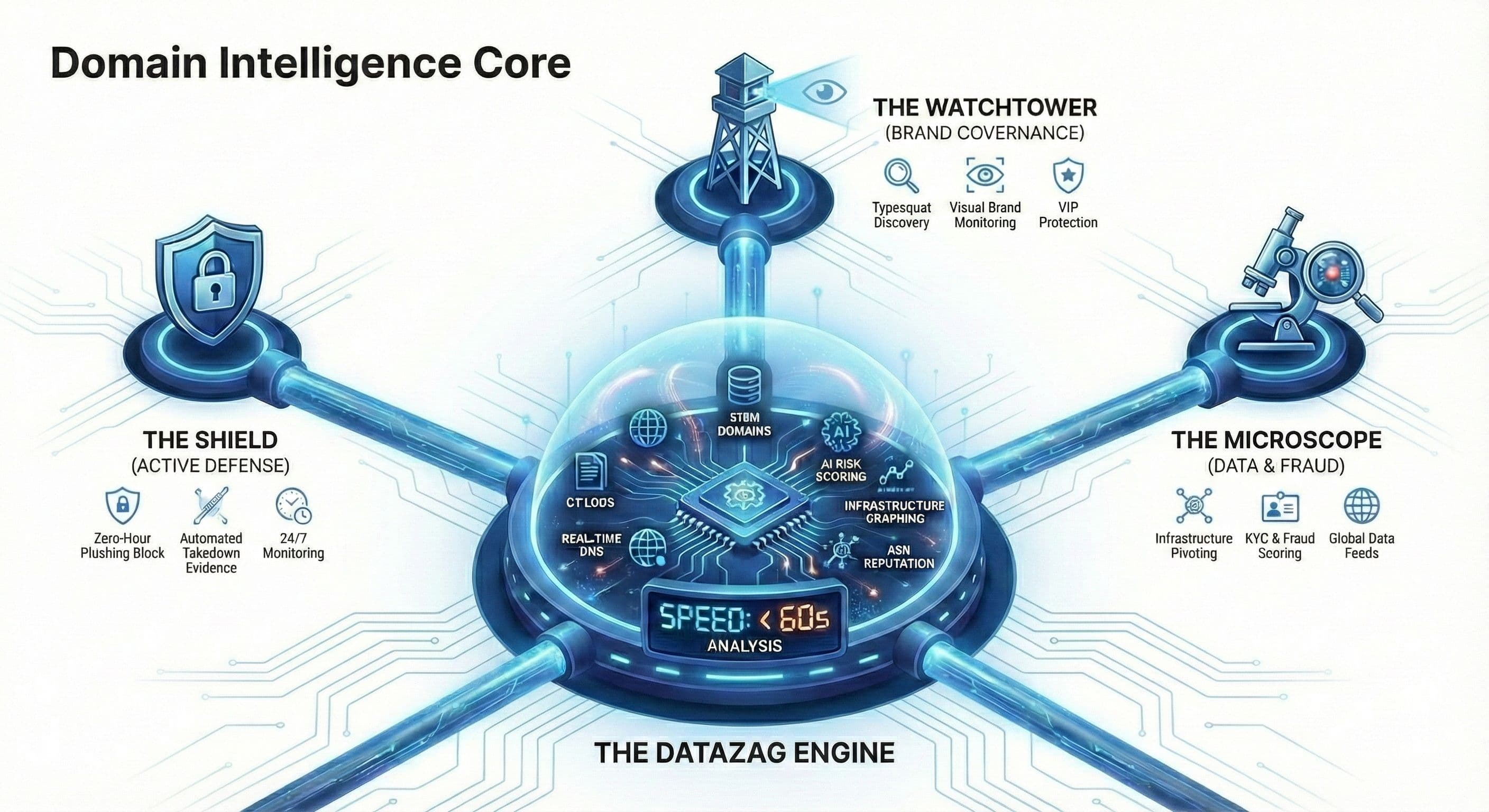
One Intelligence Core. Total Internet Visibility
Datazag operates a continuously refreshed intelligence backbone spanning 315M+ domains and global infrastructure.
Delivered via API or webhooks, designed for automated enforcement — not manual investigation. Plus access to our 315M+ domain database using Cloud Shares.
Our Approach:
Business outcomes
Faster decisions. Less analyst time. Fewer false positives.
Investigations in minutes, not hours—complete data and automated evidence for fast, accurate decisions.
Reduce triage workload
Prioritise domains with meaningful risk signals, reducing time spent on low-value candidate investigation.
Improve accuracy
Explainable risk factors and contextual enrichment help reduce false positives and support defendable decisions.
Detect earlier
Identify suspicious domain infrastructure before active abuse, enabling faster investigation and response.
Integrate into existing workflows
Deliver enriched signals via API, feeds, or webhooks into SIEM/SOAR and case management tools, helping shorten time-to-action.
Choose Your Path
All offerings are powered by the same real-time infrastructure profiling engine — the difference is how you apply it.
Threat Detection
Detect infrastructure threats before attacks launch
What you get:
- •Sub-60-second threat detection during infrastructure setup
- •<1% false positive rate
- •SIEM/SOAR integration (Splunk, Microsoft Sentinel, Elastic)
- •API or Cloud Share access for enrichment
- •Detection of phishing, C2, fraud, and email abuse infrastructure
Who this is for:
- SOC and security operations teams
- Fraud prevention teams
- Email security teams
- Threat intelligence analysts
Stop threats before they launch by detecting phishing infrastructure, C2 domains, fraud campaigns, and email abuse during setup — not after victim reports.
Brand Protection
Detect brand impersonation before customers are targeted
What you get:
- •Continuous monitoring of brand-linked infrastructure
- •Visual similarity detection with forensic screenshots
- •Evidence packages ready for takedown and enforcement
- •Alerts via email, Slack, and Teams
- •Executive and senior-leader impersonation tracking
Who is for:
- Brand protection teams
- Marketing and communications teams
- Legal and compliance teams
- Customer trust and safety teams
Detect lookalike domains, credential harvesting sites, and brand abuse at infrastructure creation — before phishing emails are sent or sites go live.
Domain Intelligence
Query predictive risk signals directly in your data warehouse
What You Get:
- •315M domains in Snowflake, Databricks, AWS, Azure & Google Cloud
- •Hourly incremental updates (Delta/Iceberg)
- •No API rate limits (query as needed)
- •JOIN-ready schemas for analytics
- •50+ infrastructure, risk, and attribution attributes per domain
Who is this for
- Data engineers and analysts
- Security data scientists
- Developers and DevOps teams
- Risk and fraud data teams
nrich logs and datasets with real-time domain risk, hosting intelligence, and attacker signals — using SQL, not APIs.
Partners
Build premium security services without building the infrastructure
What You Get:
- •Partner portal to mange customers and services
- •40-50% resale margins
- •Founding Partner pricing (limited time)
- •Technical enablement and co-marketing
Who this is for:
- MSSP & MDR partners
- ESPs & Email platforms
- Ecommerce Platforms
- Strategic & technology integrators
Deliver phishing detection, brand protection, and email security services powered by predictive infrastructure intelligence — without operating the detection stack yourself.
Domain intelligence is more than just phishing attack detection
Our 315M enriched domains with risk scores, hosting intelligence, and real-time updates can support your other cyber security needs
Fraud & Platform Abuse Detection
Detect newly created bad actor infrastructure commonly used in scams and account fraud.
Security Operations Enrichment
Feed early-warning domain signals into SIEM?SOAR workflows.
Vendor & Supply Chain Monitoring
Continuously monitor third-party domains for emerging risks.
Email Security and Deliverability
Identify spoofed sender domains and suspicious infrastructure including SPF and DMARC records.
Threat Intelligence and Hunting
Detect C2 infrastructure and threat actor domain patterns.
Attack Surface Management
Discover external assets and shadow IT infrastructure, plus sub-domain sprawl.
Stop phishing infrastructure before it’s used
Start with transparent pricing or integrate enterprise feeds into your existing stack.
Transparent pricing, explainable signals, and flexible delivery via API, feeds, or webhooks.